Infosec managers are the backbone of any organization's cybersecurity efforts. You juggle multiple tasks, from managing security tools and patching vulnerabilities to ensuring regulatory compliance and leading your security team. Squad1 empowers you to streamline these processes, prioritize threats effectively, and demonstrate the value you bring to the organization.
Your team is bombarded with a constant stream of vulnerability alerts. Squad1 VM's intelligent filtering and risk-based scoring help you focus on the most critical vulnerabilities first, reducing alert fatigue.
You need to manage vulnerabilities with a limited budget and tight deadlines. Squad1 VM automates repetitive tasks, freeing up your team's time to focus on strategic security initiatives.
Security leaders often struggle to quantify the value of security investments. Squad1 VM's comprehensive reporting helps you demonstrate the effectiveness of your vulnerability management program and its positive impact on the organization's security posture.
The cyber threat landscape is constantly changing. Squad1 VM's continuous vulnerability scanning and threat intelligence feeds keep you informed about the latest threats, allowing you to be proactive in your defense strategy.
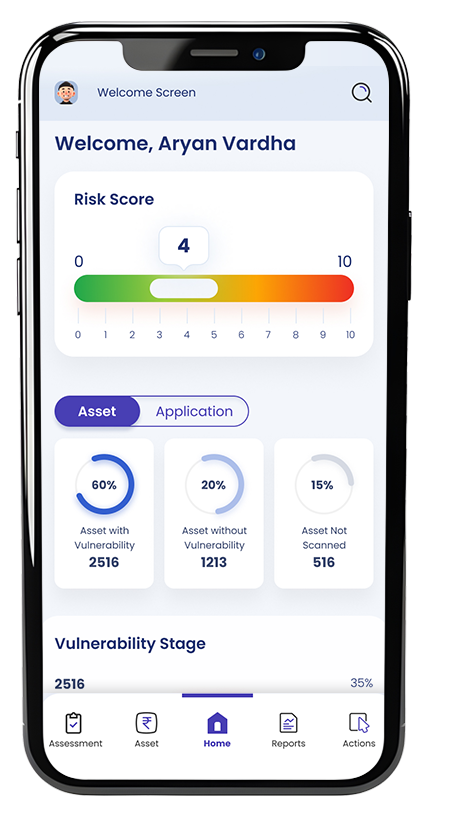


Focus on the vulnerabilities that pose the greatest risk to your organization based on exploitability and potential impact.
Streamline vulnerability scanning, prioritization, and patch deployment tasks, freeing up your team's time for critical security initiatives.
Generate detailed reports that showcase the effectiveness of your vulnerability management program and its contribution to overall security posture.
Stay vigilant with continuous updates on threats and vulnerabilities through ongoing threat intelligence feeds, empowering implementation of preventive measures.






Engage in a brief discussion for tailored security assessments, live product demo showcasing SQUAD1's integration capabilities with premium security scanners and explore customized Security Assessment workflows—all with no commitment necessary.




